本部办的面向新手的比赛,为了积极响应一校三区的团结精神就抽了两天冲了冲榜,最终rank #7.这里只挑一些我觉得有意思的题目写一写wp.
Crypto题目太少了!
Crypto
Yamato
出题人把题目名字打错了,故本wp未采用原题名XD
task.py
1 | import time |
msg和ciphertext太长就不放了,总之这个长度足够取出624个32bit,所以一眼预测MT19937.
不过,我猜出题人不知道多个MT19937的异或依然是MT19937,所以才会特意给出其中一个流的seed(甚至还在注释里调皮😡)
为什么呢?因为MT19937的twist过程和异或是结合的,而异或甚至还是交换的,所以多个MT19937异或之后还是一个MT19937.这样我们直接把题目中两个流的输出拿去randcrack就可以了,根本不需要爆破出题人藏起来的seed🤣
exp
1 | from randcrack import RandCrack |
当然,如果硬要爆seed,你会发现出题人用的seed刚好就是2019-01-01 00:00的时间戳.
Feistel Collision
task.py
1 | from param import * |
param.py
1 | PI = [58, 50, 42, 34, 26, 18, 10, 2, |
大概看了看貌似用的几个box都是DES原版,所以问题大概不会在param.py里.输出的是定长8字节,所以碰撞是必然存在的.
对DES熟悉的朋友知道,DES的64bit key里只有56bit是有用的,这题其实也是一样:
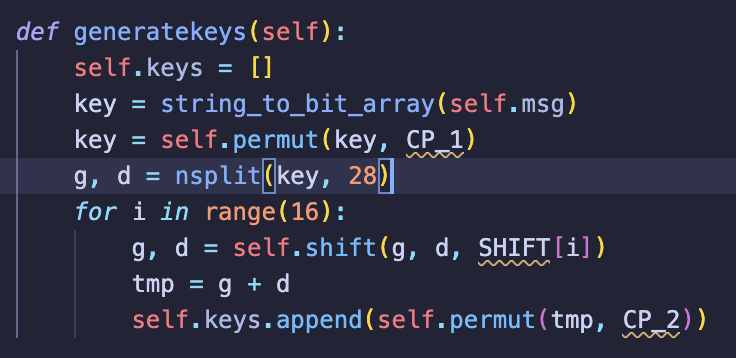
所以合理猜测改动原消息中的某个字节,得到的hash应该就能碰撞了.
exp
1 | from param import * |
榴莲披萨
task.sage
1 | from Crypto.Util.number import * |
取R=A,msg=b"Durian Pizza",然后就是Matrix DLP,直接看exp吧.
exp
1 | from Crypto.Util.number import * |
Misc
神秘文件
给了个以PDP-11的端序存储的数据,按wiki上对PDP-11端序的描述调了一下然后乱搞一通就出了XD
exp
1 | data = [1819497543,1312250199,1383555909,1316313210,2017614407,961176172,963137110,1232623666,964322374,1227908168,1684821101,1178159443] |
宇宙的回响
一耳朵就知道是反相+sstv.但是双声道直接反相是不行的,因为两边混入的噪声的响度不一致.把左声道响度降低18.5dB后反相相加,然后sstv decode成功.
exp
1 | import numpy as np |
decode出来一张Aztec Code

Google Play上找到一个Aztec Scanner的App,下载安装扫码get🥰
总结
满打满算应该是做了3天题,最后还能再出大概两三道,但是要赶毕设和备课就摆了,对我来说Crypto AK就已经心满意足了~
Tiny Image那题有点可惜,虽然想到要对bmp的后12字节数据动刀子但是试了两三次都莫名其妙地过不去后端的文件结构校验,后来也没继续尝试.修修补补也是知道要动调改rip去让它吐flag,但是那天在实验室带的是Macbook没有对应环境,后面回宿舍的时候又过去了做题的热情,200分就这么不了了之.
密码出得挺有意思,榴莲披萨差不多做了一个小时才出,本来以为Matrix
DLP这种套路能一把梭的,结果还是有思维漏洞--只用Jordan标准型中的一个对角线元素去求得的DLP未必就一定是矩阵本身的DLP.中间又细致地处理了multiplicative
order的问题,最后才成功解出.(不过解出后发现只用一个对角线元素求也是可以的,只是我用的那个不是该用的那个QAQ)Yamato貌似用了非预期解,而且感觉比预期还要巧妙XD
唯一有点不爽的就是Crypto题目数量与其他方向相比明显偏少,气抖冷,我们密码什么时候才能站起来😡
