imaginaryCTF round46
Misc
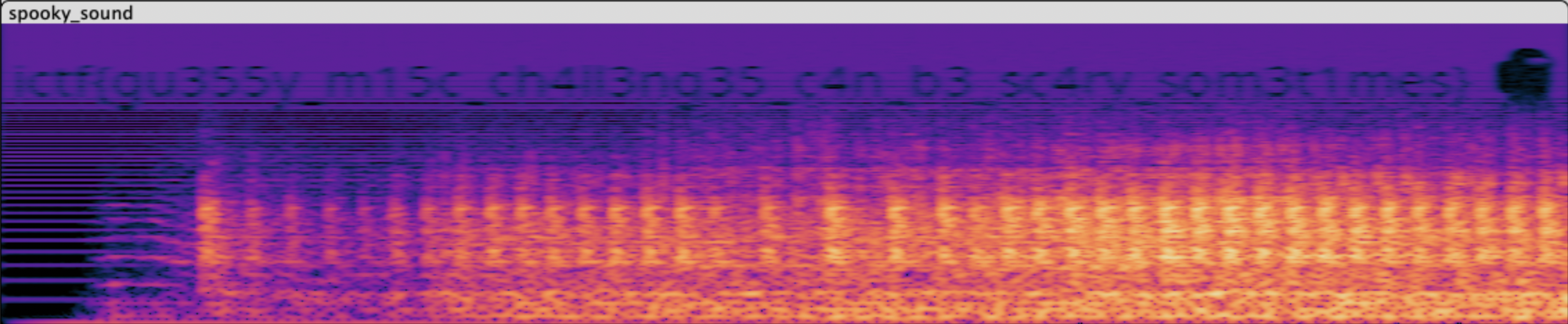
Spooky Sound
wav,先拖下来Audacity看一眼频谱,果然就有flag。
Last Minute
1 |
|
直截了当的爆破。
1 |
|
Crypto
xorsar
hbugzchu^gmhqqhof^guv>^0e8c3028|
实验可知
Random Base
OED8WECRFCS6/TC9$DUICGPEFQEGS6BM6*.CN-DZ2
字母特征猜出是base45。
Strange Base
aQ==Yw==dA==Zg==ew==dg==Mw==cg==eQ==Xw==NQ==Nw==cg==NA==bg==Zw==Mw==Xw==Yg==NA==cw==Mw==Xw==Ng==NA==IQ==fQ==
很容易看出来是逐字符的base64,4字一组decode即可。
So much XOR
1 | from pwn import xor # pwntools xor function |
异或满足交换律和结合律,并且和同一个数异或两次会还原自身,所以做的这么多异或无非就是异或了0次或者1次。
1 | from pwn import xor # pwntools xor function |
Reverse
Tape Reader
程序会简单地读取纸带做对应操作。纸带和操作都明确给出了,逆操作即可。需要注意的是,Binary Ninja似乎解析纸带数组时会出现错误,这部分最好用IDA去做。
1 |
|
