这次羊城杯手感不错,密码AK同时还拿了两个一血和一个二血。
但是没有血分奖励,白忙活
Update: 没有白忙活!主办方看起来严查Wp了,ban了不少作弊队伍,也是成功递补进入决赛了😋
Crypto
TH_Curve
task
1 | from Crypto.Util.number import * |
检索一些资料可以知道题目用的曲线是Twisted Hessian Curve,用projective
coodinate可以把
检查曲线的order可以知道转换后的曲线的order里有一个大因子,而flag并不长,所以直接在子群上求解ECDLP即可。
exp
1 | # copied from https://blog.maple3142.net/2023/07/09/cryptoctf-2023-writeups/#barak |
BabyCurve
task
1 | #!/usr/bin/env python |
我并不知道第一条是什么曲线,本来以为没办法处理DLP但是队友@SinzoL告诉我c和d都很小所以可以直接爆破XD
c=35 b=98
得到c和d之后检查第二条曲线的order可以发现order = p+1,直接MOV Attack起手:
exp
1 | def find_embedding_degree(E): |
RSA_loss
task
1 | from Crypto.Util.number import * |
m>n所以直接解密会失败,因为拿到的是m%n。不过因为有很明显的线性关系
所以直觉上很容易想到格。
鸡块师傅出过一些类似的题目,但是在本题中既没有flag的长度也没有flag的字符表。好在字符表大概可以猜到,所以仿照这篇文章的手法减去字符表的均值后得到的向量也还算短,那么只需要爆破一下长度就好了。
我这边是顺着这个思路走下去用fplll做的格枚举,免去不少麻烦。
exp
1 | import string |
为什么这题能有这么多解,感觉难度并不算很低啊QQ
TheoremPlus
task
1 | from Crypto.Util.number import * |
由Wilson定理一眼丁真出decode_e()函数的返回值是
所以你告诉我这么简单的初等数论解出来的人数比两道ECC还少?原来你们不用学初等数论就能玩近世代数是吗.jpg
Re
你这主函数保真么
找到加密逻辑后喂给GPT得知加密方式是离散余弦变换(DCT),让GPT搓个脚本出来直接秒了。求出来之后还要ROT13一下。
exp
1 | import scipy.fftpack |
docCrack
想编辑宏但是提示有密码,参考这篇文章bypass掉之后看到一坨代码:
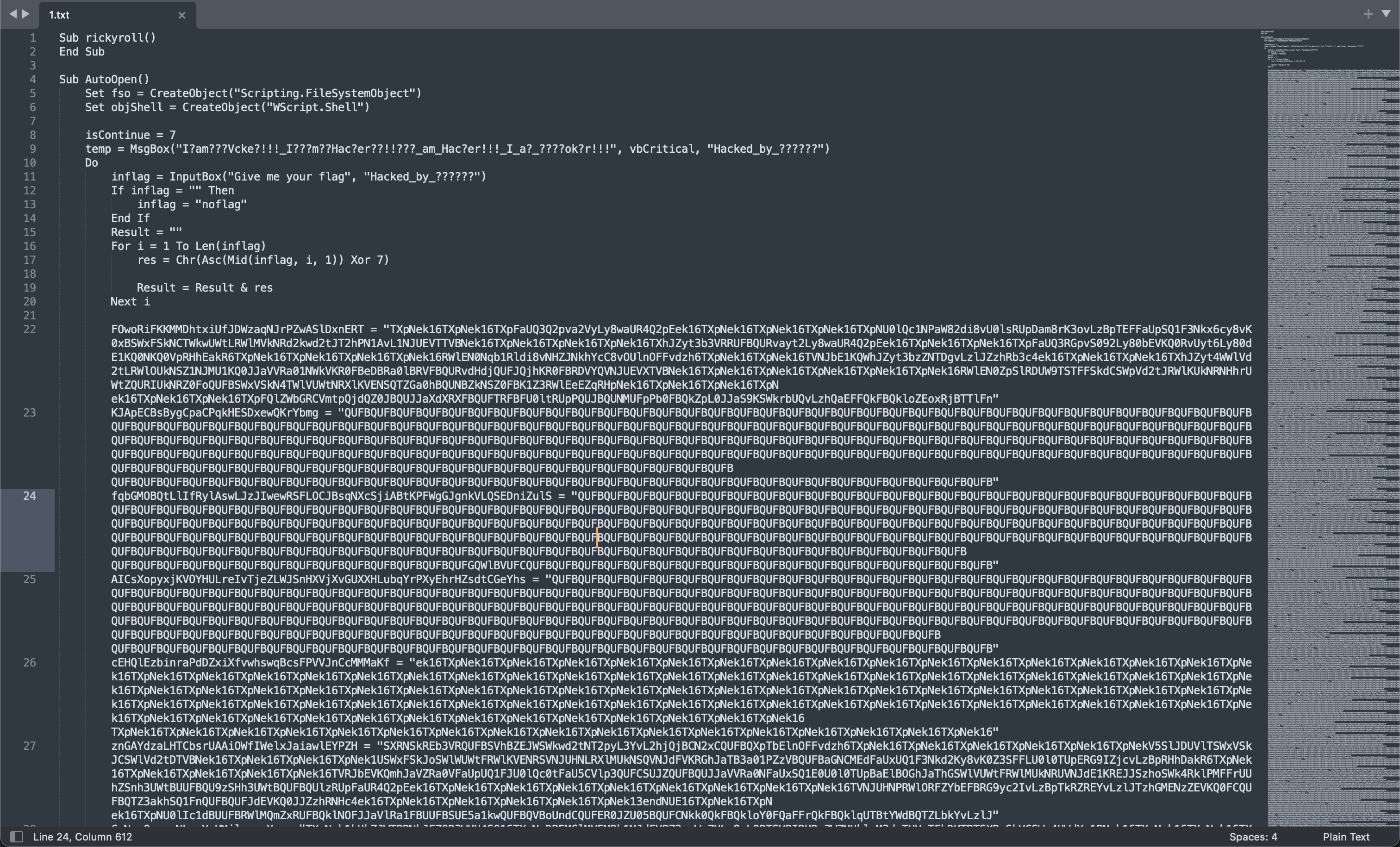
懒狗如我当然不会选择去嗯逆这一坨,正好后面有这么一段:
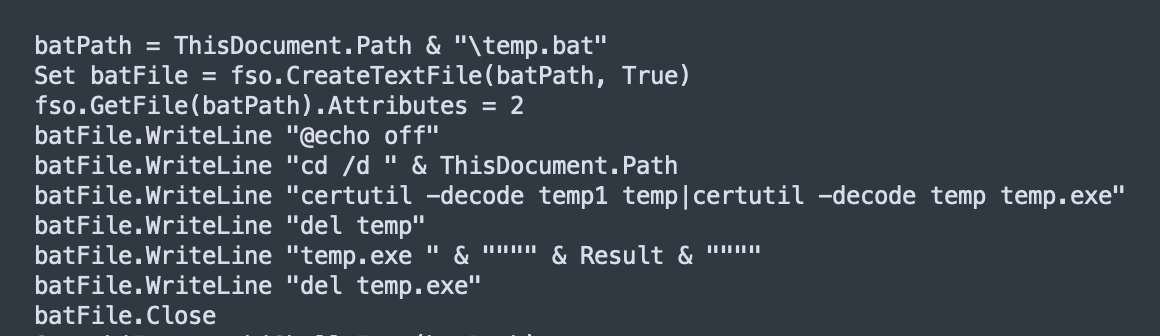
OK,找个云沙箱跑一下把生成的二进制拖下来就好了。这个二进制还是很容易逆的:
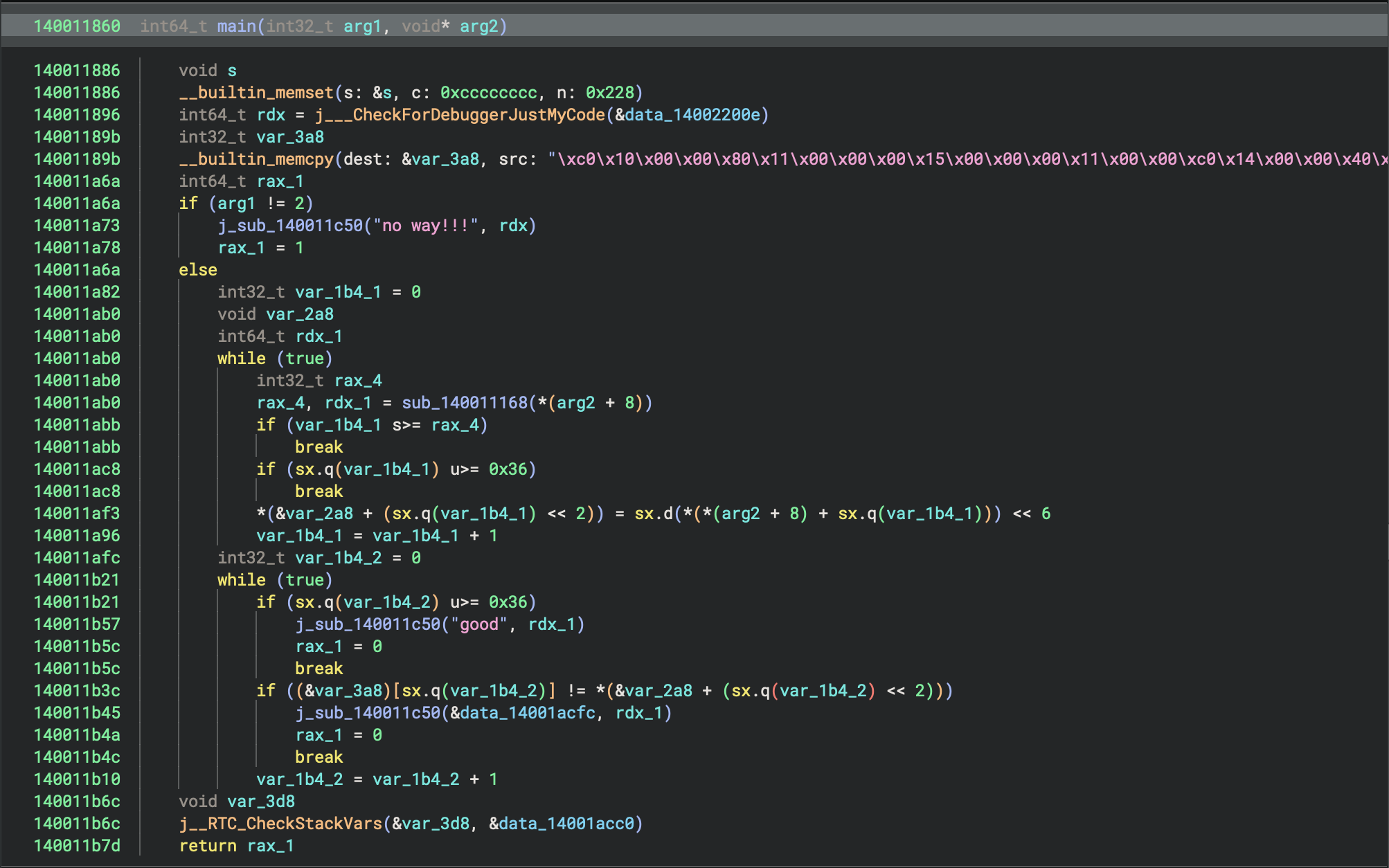
exp
1 | c = [4288,4480,5376,4352,5312,4160,7936,5184,6464,6528,5632,3456,7424,5632,6336,6528,6720,6144,6272,7488,6656,7296,7424,2432,2432,2432,5632,4416,3456,7168,6528,7488,6272,5632,3520,6208,5632,4736,6528,6400,7488,3520,5632,5184,3456,7488,7296,3200,6272,7424,2432,2432,2432,7808] |
Pic
魔改的RC4,5字符密钥长度。因为png文件前16字节都相同所以拿这个作为判断准则,搓个脚本爆一下:
1 | import itertools |
吐出来的第一个key正好就是target key。
